Background
The Security Research team at Promon was alerted by i-Sprint, a longstanding partner, to a recent occurrence of Android malware in Southeast Asian countries such as Indonesia, Thailand, and Vietnam. Along with these targeted areas, it is suspected that the malware has also affected Singapore and Malaysia. This form of malware operates through messaging platforms and utilizes social engineering tactics to deceive banking clients. In conversations with banks in this region, Promon discovered an unfortunate incident where one customer lost 10 million Thai Baht (equivalent to $280,000) due to this scheme.
Promon had obtained a sample of this malware from an end-customer’s device, specifically designed to attack one particular bank. However, it also contains code that could potentially target other banking applications. Despite extensive efforts, additional samples and public information about this specific malware were unavailable, leading to their own technical analysis. The presence of Android banking malware has been ongoing for some time now, with new families being uncovered regularly. What sets this particular malware apart is its use of virtualization as a means of attacking applications – a tactic not commonly seen among other malicious software. Traditionally, virtualization has been utilized for reverse engineering purposes.
How FjordPhantom malware spreads
The malware spreads primarily through email, SMS, and messaging apps called FjordPhantom. The user is prompted to download an app resembling their own bank app. It contains the real bank’s Android app, but it runs in a virtual environment with additional components that allow it to be attacked.
Once the app is installed, users are contacted by call center team who pose as bank customer care and instruct the user about the process. During this time they have access to users device and either complete the transaction and steal the credentials for further use.
How FjordPhantom malware uses virtualization
To perform its attacks, the malware embeds a virtualization solution and a hooking framework from open source/free projects found on Github.
In recent years, virtualization has become quite popular on the Android platform. It allows apps to be installed and run in virtual containers. Since many of these apps can be downloaded from the Google Play Store, Google accepts them since there are legitimate reasons for using such solutions. Installing the same app multiple times for logging into it with different accounts is a popular reason for using these solutions. This is not possible on Android.
Virtualization breaks the Android sandbox
Potential danger of loading apps in virtual containers is that it breaks Android Sandbox. Each app usaully operated in its own isolated sandbox in Android. But with virtualization multiple apps are able to work in same sandbox and access each others files and memory. This makes virtualization a handy tool for attackers, with which they can bypass rooting of device to break the sandbox. Installing multiple apps in same sandbox removes the need for rooting thus being not detected by security measures.
How FjordPhantom works
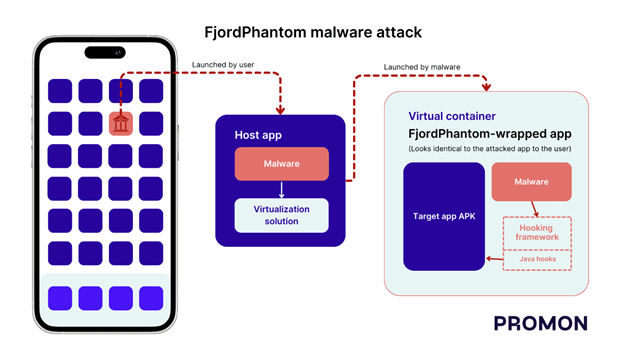
Image Source: Promon
Prevention
The FjordPhantom malware is a sophisticated Android malware used to commit real-world fraud. Users should exercise caution when downloading apps from untrusted sources.


